

The data the boot generates is fed into a machine-learning model, which in turn tunes the device to personalize its support, applying force at the ankle...

The main function of MLOps is to automate the more repeatable steps in the ML workflows of data scientists and ML engineers, from model development and...
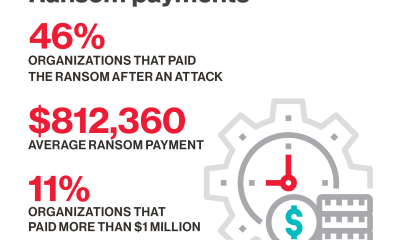

“Triple extortion” or “quadruple extortion” attacks, which additionally incorporate distributed denial of service (DDoS) attacks or threats to third parties, are now also part of the...


Rebecca George doesn’t mind the vultures that complain from the trees that surround the Western Carolina University body farm. Her arrival has interrupted their breakfast. George...


Come back to this page for rolling updates throughout the day as we kick off ClimateTech, MIT Technology Review’s first ever conference dedicated to finding solutions...


The US finally stepped up as a leader in climate action, enacting a trio of major laws that could add up to the largest federal investment...


Take ribs, for instance. George stood near a donor, almost entirely skeletonized, whose ribs were cracked. One might surmise that these broken ribs were a clue...


So its current strategy seems to be to release a string of updates to see what might get people interested—a “throw spaghetti at the wall and...


Chin: Yeah, within the same year, the police were using that technology to track suspects, and they basically openly said: “Well, we changed our minds.” Lin:...


Mexico has long struggled with a history of kidnapping. As of October 5, there were 105,984 people officially listed as disappeared in Mexico. More than a...