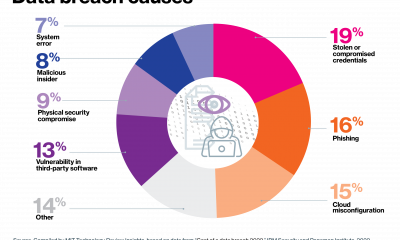
This greatly expanded attack surface can spell bad news for companies that aren’t properly equipped to defend themselves against cybersecurity threats. Globally, the average data breach...


Broadly speaking, Belmonte says he believes “dysregulation” of these control systems is the fundamental process that underlies aging and many diseases. To rejuvenate cells, Belmonte has...


Thank you for joining us on “The cloud hub: From cloud chaos to clarity.” Darren Kane, chief security officer with nbn Australia, discusses Australia’s mission to...


In the months after Vladimir Putin announced the invasion of Ukraine, Russia saw a mass exodus of IT workers. According to government figures, about 100,000 IT...


“I think this is going to be pretty much a disaster from a security and privacy perspective,” says Florian Tramèr, an assistant professor of computer science...


Thank you for joining us on “The cloud hub: From cloud chaos to clarity.” Chaos engineering is a new approach to learning about systems by breaking...


Thank you for joining us on “The cloud hub: From cloud chaos to clarity.” Vishal Salvi, from Infosys, and Steve Durbin, from Information Security Forum, have...


Machine learning security is business critical ML security has the same goal as all cybersecurity measures: reducing the risk of sensitive data being exposed. If a...
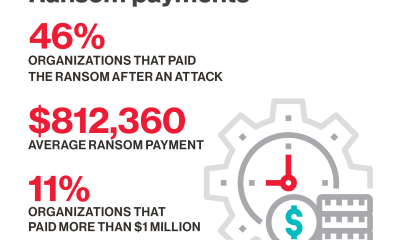

“Triple extortion” or “quadruple extortion” attacks, which additionally incorporate distributed denial of service (DDoS) attacks or threats to third parties, are now also part of the...


Thanks to his distinctive style, Rutkowski is now one of the most commonly used prompts in the new open-source AI art generator Stable Diffusion, which was launched...
Recent Comments